Known Issues and Workarounds#
S3 Mounts with a / object in the bucket breaks connection in Nucleus
If you have a / object (slash with no other characters before it), this will cause Nucleus to fail to mount the bucket.
Workaround: Rename so it containers character (e.g. abc/) or delete that object.
Cache size sometimes does not update to reflect actual disk space used by the Cache
The Cache size may show as empty and using no disk space when it is in fact using storage space for cached files. This is an intermittent issue and we are working towards a solution.
LevelDB database has become corrupt
We use LevelDB as our underlying datastore. LevelDB is a fast database that outperforms its peers in write operations and sequential-order read operations. However, in rare cases with improper shutdown the underlying LevelDB database can become corrupt. We recommend frequent backups to avoid this scenario.
Unable to Send Authentication Results Back
Most likely you are reading this page due to having received the following Nucleus error message in your browser:
Unable to send results back to the application that initiated the authentication.
Why
We are aware of this problem impacting some customers with recent versions of Chrome web browser. It has to do with internal changes to built-in flags’ configuration of Chrome.
While we are working on the ultimate fix for this problem, we offer workarounds as detailed below.
This problem will affect Chrome versions released around and after September 2021.
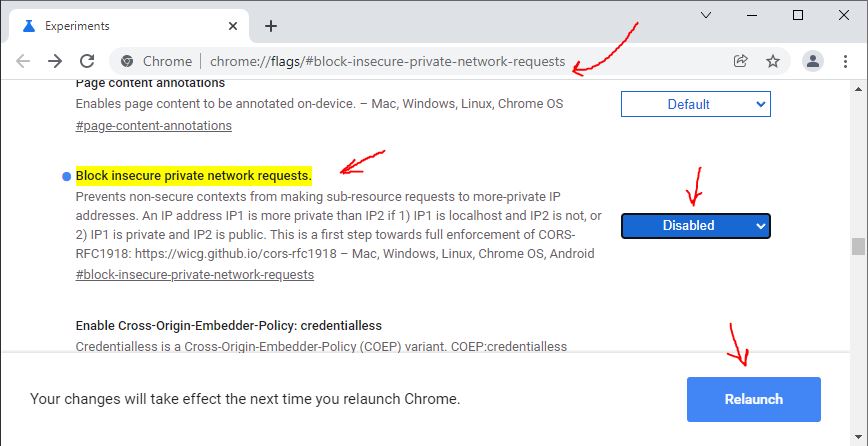
To work around this, disable the Block insecure private network requests
flag.
Copy the following into your clipboard:
chrome://flags/#block-insecure-private-network-requestsOpen up a new tab in Chrome. Paste the
chrome://...link into the address bar of that tabThe flag will open and be highlighted. Change it to
DisabledRe-launch Chrome
This problem should not be affecting Edge. Please contact your NVIDIA representative if affected by it while using Edge.
This problem should not be affecting Firefox. Please contact your NVIDIA representative if affected by it while using Firefox.
You may attempt the same workaround as for Chrome (above). Please contact your NVIDIA representative if workaround offered for Chrome does not help resolve the situation.
Detailed Description of the Problem
When a Client (App or Connector) wants to authenticate with a Nucleus, a few things happen:
Client launches machine’s default web browser, and directs it to Nucleus’s Authentication Service
At the same time, Client creates a simple HTTP server on a random port. The port selected is passed to Nucleus’s Authentication Service as a URL parameter.
Once Authentication service completes the Authentication, it executes a small, client-side JavaScript-based HTTP request to the Client’s HTTP server. That request is how the Authentication service passes issued session tokens back to the Client.
That last bit - the HTTP call from the Browser back into the Client - is what is affected by latest Chrome updates. If Nucleus is not running SSL, the Authentication Service’s page will not be permitted to call back into the local port opened by Client.
Changing the flag outlined in the Chrome workaround above makes Chrome permit the callback.